Kubean Enters CNCF Sandbox¶
In April 2024, the CNCF community welcomed a vibrant green pod (Kubean) into the Sandbox.

Over the past few years, several developers from DaoCloud have been maintaining code in the Kubespray community. On the occasion of May Day 2022, inspired by Uncle Kai and Brother Xiao, they casually sowed a green pod Kubean in the CNCF community. This young pod, after nearly two years of diligent nurturing, began to crackle and grow, and now serves as the initial spark for the DCE 5.0 production cluster, capable of creating hundreds to thousands of clusters on demand.
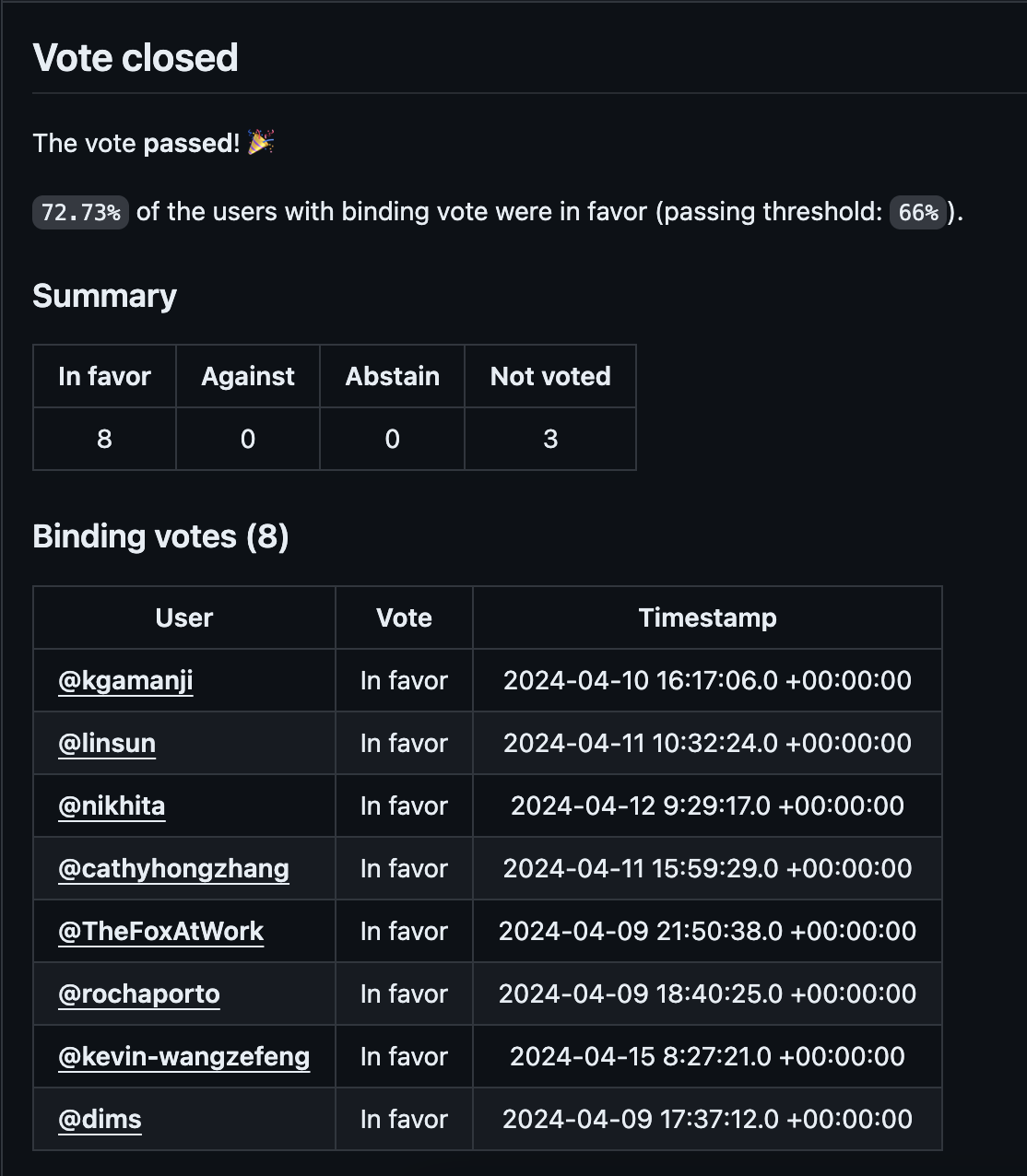
On April 15, 2024, after an 11-member CNCF TAG committee vote, with 8 in favor and 3 not voting, the results exceeded the 66% threshold, successfully entering the well-known Sandbox for further incubation.
What Can This Pod Do?¶
At its core, Kubean is an Operator, providing CR resources for containerized clusters, capable of deploying clusters and more as Jobs. Like the legendary generals who could conjure soldiers from beans, as long as you have an underlying cluster, you can deploy numerous new clusters in various environments using Kubean.
- Supports declarative deployment of clusters from scratch using Operator and Helm Chart, supports D1, D2 for efficient operations (scaling, upgrading, uninstalling, etc.)
- Capable of deploying K8s clusters on bare metal, virtual machines, cloud platforms, and more
- Supports almost all Linux distributions
- Supports log tracing for convenient cluster operations (upgrades, scaling, uninstallation), and also facilitates rolling back clusters to a specific job state
- Supports engines like Kubespray
- Supports offline installation and upgrading
Here is the overall architecture diagram of Kubean:
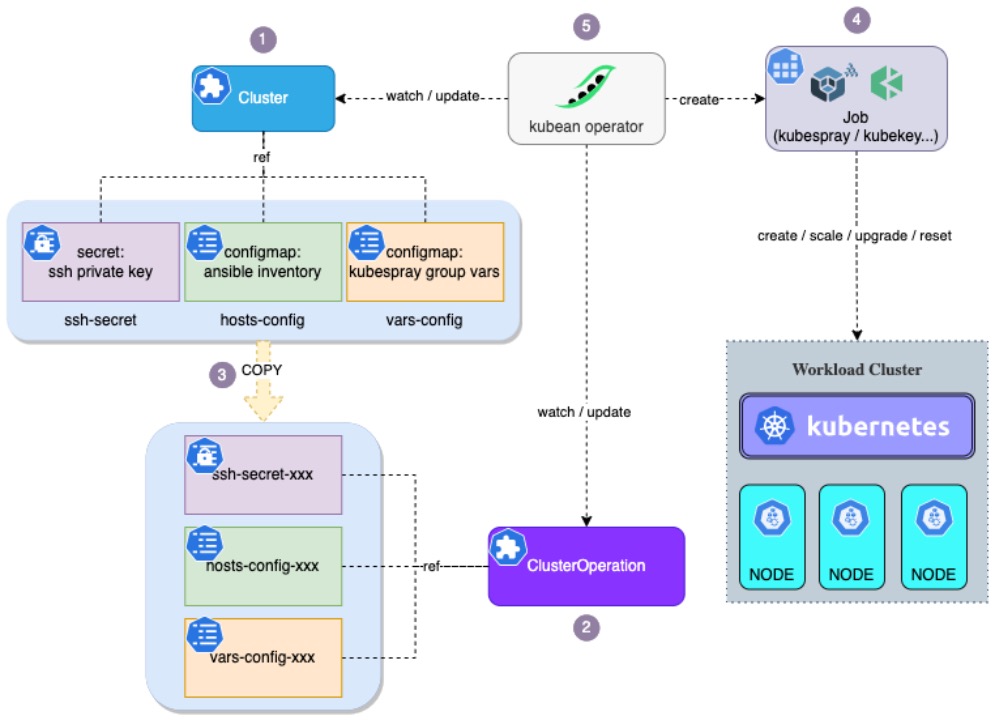
Kubean operates on an existing Kubernetes cluster, using standard CRD resources and Kubernetes built-in resources to control and manage the lifecycle of clusters (installation, uninstallation, upgrading, scaling, etc.). Kubean uses Kubespray as its underlying technology dependency, simplifying the cluster deployment process and lowering the barrier for users. Additionally, it builds on Kubespray's capabilities by adding new features like operation records and offline version tracking.
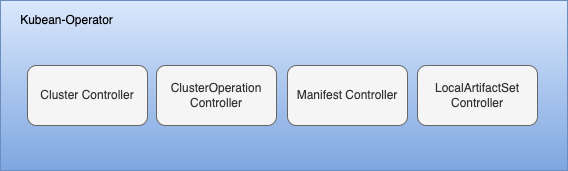
This pod consists of four beans:
- Big Bean Cluster Controller: Monitors the Cluster object. Uniquely identifies a cluster, possesses access information, type information, deployment parameters of the cluster nodes, and associates all operations (ClusterOperation objects) on this cluster;
- Second Bean ClusterOperation Controller: Monitors ClusterOperation objects. When a ClusterOperation Object is created, the controller assembles a Job to execute the operation defined in the CRD object;
- Third Bean Manifest Controller: Monitors Manifest objects. Used to record and maintain the current version of components, packages, and versions used and compatible with Kubean;
- Fourth Bean LocalArtifactSet Controller: Monitors LocalArtifactSet objects. Used to record the supported components and versions of offline packages.
Comparison with Similar Products¶
Kubean currently defaults to the Kubespray underlying engine, but plans to support more engines in the future, such as switching to newer engines like Kops and KubeKey.
Kubespray is part of the kubernetes-sigs ecosystem, designed for deploying production clusters as an open-source project. Kubean was initially developed based on Kubespray, but has since added several new features. Below is a simple comparison between Kubean, Kubespray, Kops, and KubeKey:
| Kubean | Kubespray | Kops | KubeKey | |
|---|---|---|---|---|
| Applicable Scenarios | Suitable for cloud-native declarative API cluster management scenarios | Suitable for complex scenarios with varying deployment platforms | Suitable for fixed infrastructure platform management | Suitable for lightweight dependency deployment scenarios |
| Containerization Support | Supported | Supported | Not Supported | Not Supported |
| CLI Support | Not Supported | Supported | Supported | Supported |
| Declarative API | Supported | Not Supported | Not Supported | Not Supported |
| Supported Deployment Platforms |
|
|
| Unknown |
| Mixed Architecture Support | Supported | Supported | Not Supported | Not Supported |
| Offline Deployment | Supported | Supported | Not Supported | Supported |
| Implementation Method |
|
|
|
|
| Operating System Support |
|
| Depends on infrastructure support |
|
| Runtime Support |
|
|
|
|
| Upgrading | Supported | Supported | Supported | Supported |
Sandbox Journey¶
Kubean was selected for the CNCF Landscape in late July 2023 and immediately applied to join the Sandbox.
At the end of August, ErikJiang, the main maintainer of Kubean, presented a PPT online to CNCF TAG-Runtime members during a regular hearing, introducing the origins, functional features, and future plans of Kubean.
In the following months, he answered many questions raised by TAG members, such as the differences from Cluster API, enhancing the persuasiveness of Kubean's ease of use. Subsequently, TAG committee members jberkus, caniszczyk, rochaporto, and others proposed new schemes regarding Kubean's affiliation:
- A subproject under kubernetes-sigs/kubespray
- Or as an independent Sandbox project
Open source progresses through exchange and collision, and so does Kubean. This pod was originally born on the branches of Kubespray, but now it has been found to be capable of further development based on more engines, alleviating the TAG committee's concerns. In fact, it is not only an extension of Kubespray but can also be an expansion of more cluster lifecycle engines; it is a new product running on old-era engine technologies, endowed with a new mission.
In early April 2024, raravena80 on behalf of TAG decided to accept Kubean into the sandbox, initiating the voting process.
On April 15, 2024, the TAG votes exceeded the 66% threshold, and Kubean began the Sandbox Onboarding process.
Behind the Scenes¶
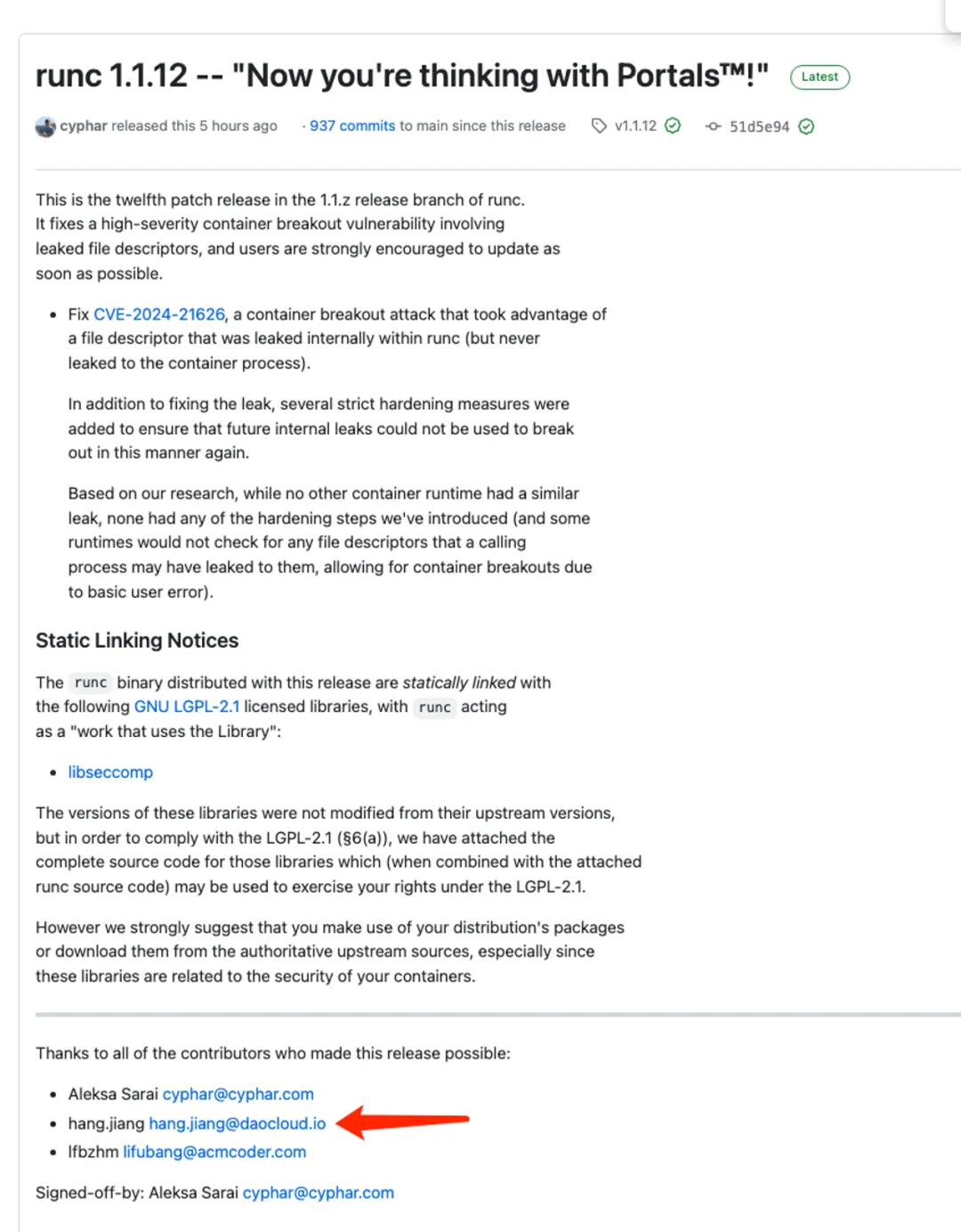
One small incident worth mentioning is that in early 2024, Jiang Hang, a code maintainer of Kubean, opened GitHub during a weekend to routinely review open-source code and incidentally discovered a runc container escape vulnerability. He raised an issue, discussed it with several community developers, and then submitted a PR to fix this CVE vulnerability. Later, this vulnerability, identified as CVE-2024-21626, scored a high 8.6 points, claimed to be the most severe vulnerability in runc history. See K8s runc discloses 8.6 point highest historical security vulnerability.
It was after the Kubean project team members deeply participated in and fixed this most severe vulnerability that the TAG committee's attitude softened, recognizing the value of Kubean and its team.
In summary, the open-source community always rewards effort, whether it's project recognition or personal skill and insight growth. On this global stage, efforts will be remembered. Today, there's the remarkable presence of the green pod, and perhaps tomorrow, the song of the blue sprite will be sung far and wide.
More developers are welcome to contribute and build a thriving community. GitHub project address: https://github.com/kubean-io
In Conclusion
In this world, no method can fully satisfy both the Buddha and your beloved.